Salesforce Security: A Dive into Single Sign-On (SSO) Concepts
We are continuing on our enlightening journey discussing browser-based authentication and authorization. Today, we're delving deeper, unraveling the intricate web of Single Sign-On (SSO) and the concept of an external Identity Provider controlling Authentication into Salesforce.
Salesforce as the Identity Provider
Step 1: Authentication is established through Salesforce authentication server
Step 2: A session is generated, leading you to the instance web server.
Step 3: Authorization is then granted, enabling access to pages and resources.
However, what if another system manages the authentication? Here's where third-party Single Sign-On comes into play.
High level Authentication flow for external Identity Provider (IdP)
Third-Party SSO: A Bird's Eye View
In situations where a third-party serves as the identity provider:
Step 1: Authentication is performed by the 3rd Party Identity Provider (IdP)
Step 2: A SAML assertion token is relayed to the Salesforce authentication server.
Step 3: Upon validation, this session lets your browser access the Salesforce instance web server, and subsequent authorization unfolds.
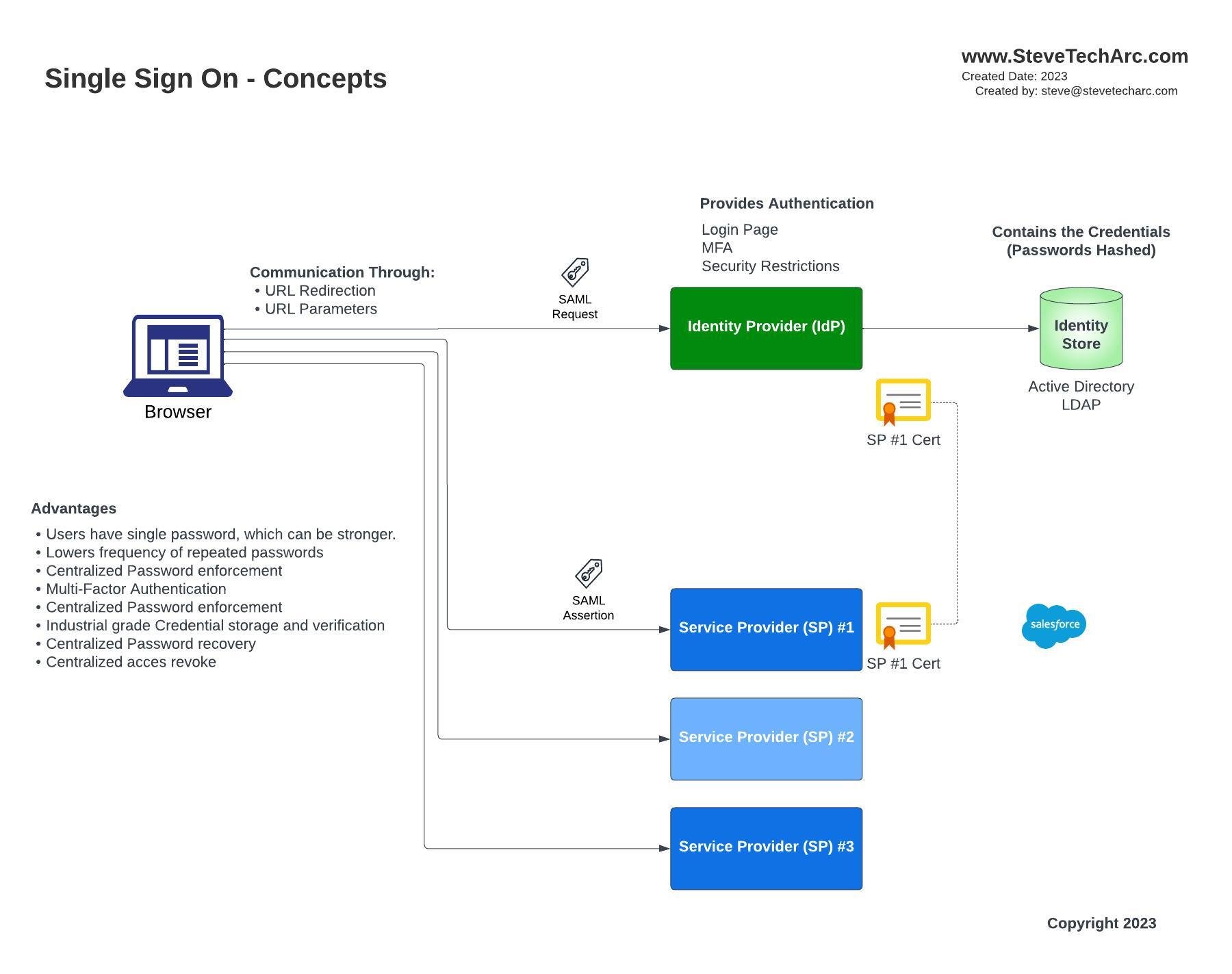
Decoding the SSO Terminology
High level view of Single Sign-On with multiple Service Providers
Service Provider (SP): This refers to platforms such as Salesforce, Workday, or any secure system unified under a single Identity Provider (IDP).
Identity Provider (IDP): The central identity hub, typically an industrial-grade system, manages the authentication for users.
Identity Store: A vault, either within Salesforce or an external entity like Active Directory or LDAP, holds the credentials. Crucially, passwords are stored in a hashed format for heightened security.
Digital Certificate: This is used to establish a trust relationship between the Identity Provider (IDP) and Service Provider (SP), ensuring seamless and secure handoff.
SAML Assertion: Exchanged between the IDP and SP, these tokens confirm a user's identity.
Benefits of Single Sign-On
Simplified User Experience: With a single IDP governing multiple service providers, users only need one set of credentials, reducing password fatigue and the risk of weak passwords.
Centralized Security: An overarching IDP allows consistent security standards, ensuring that even if one application lacks robust security mechanisms, users are still protected.
Efficient Management: In case an employee leaves or there's a breach suspicion, access can be quickly revoked from a central IDP, ensuring immediate security response.
Consistency: A single mechanism for password recovery and resetting ensures uniformity.
Single Sign-On in Action
Imagine a user beginning their day by accessing a Service Provider like Salesforce. A SAML Request gets dispatched to the IDP. Upon successful authentication, a SAML response (or SAML Assertion) is directed back to the Service Provider. This loop confirms the user's identity, offering a seamless navigational experience.
Wrap-Up
SSO stands as a key of modern-day digital security, streamlining user access across multiple platforms under the vigilant eyes of an IDP. Today, we've introduced you to the foundational concepts and benefits of SSO.
Stay with us as we dive deeper into more components in our upcoming sessions.
STA 3.3